Identity
The Identity menu group on the System Admin screen houses links to administration maintenance documents used in Kuali Identity Management (KIM) activities. They share common components and functionality with standard maintenance e-docs that are accessible from the Maintenance screen, but differ in that they are used to search for, display, and maintain tables containing information used by other e-docs throughout the KC system that is often hard-coded and static. Many offer no ability for editing via the user interface, offering just a lookup screen with search criteria and result display table only.
Basic KIM Concepts
• Persons: identify users and assign roles to them
• Groups: associate persons, roles, or other groups with each other to make role assignments
• Roles: define sets of permissions and responsibilities that users can be assigned to
• Permissions: control activities such as document editing and blanket approval activities
• Responsibilities: generate workflow action requests such as approvals
• Document Type Hierarchy: view role/group/permission/responsibility type by document
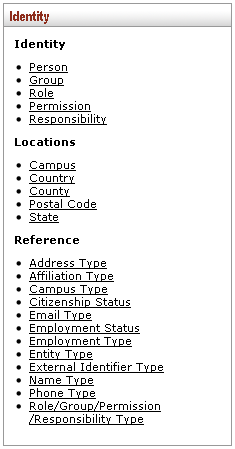
The three sections of the Identity menu group on the System Admin screen are:
: Allows you to establish and maintain user and group data along with the associated roles and permissions in the Kuali Identity Management (KIM) module for workflow purposes.
• Locations: Enables you to define valid values for various types of location information that is made available for selection throughout KC.
• Reference: Provides a means of defining valid values for use on the Person document, including types of contact and identifying information for users.
Technical Overview
Kuali Identity Management (KIM) provides identity and access management services to Rice and other applications. All KIM services are available on the service bus with both SOAP and Java serialization endpoints. KIM provides a service layer and a set of GUIs that you can use to maintain the identity information.
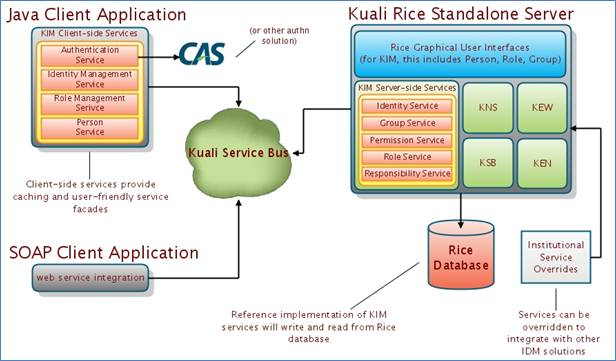
KIM is designed to be used with both Kuali and non-Kuali applications. The permissions and responsibilities it provides are defined by each user’s Role or Roles in the system. Roles can be customized to handle permissions and responsibilities in a variety of ways based on your particular needs.
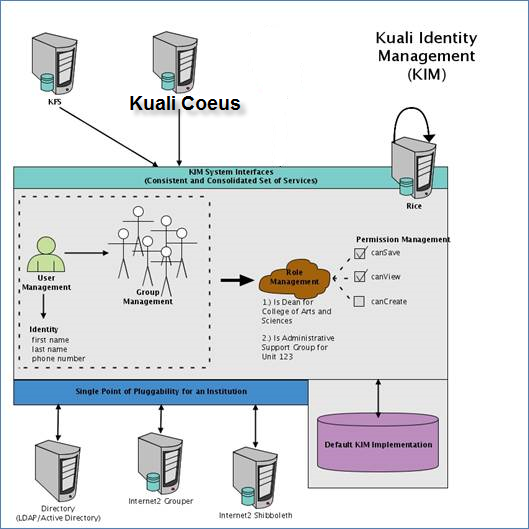
Figure 1146 Kuali Identity Management Architecture
KIM provides a reference implementation of the services but allows for customization and/or replacement to facilitate integration with institutional services or other third party identity management solutions.
KIM allows you to override one or more of its core services. For example, you could override the Identity Service, but not the Role Service.
KIM consists of these services, which encompass it’s API:
• AuthenticationService
• GroupService
• GroupUpdateService
• IdentityCacheService
• IdentityManagementService
• IdentityService
• IdentityUpdateService
• PermissionService
• PermissionUpdateService
• PersonService
• ResponsibilityService
• ResponsibilityUpdateService
• RoleManagementService
• RoleService
• RoleUpdateService
KIM evaluates permissions through its permission service. KIM provides plug points for implementing custom logic for permission checking, such as permission checks based on hierarchical data.
 Identity
Identity